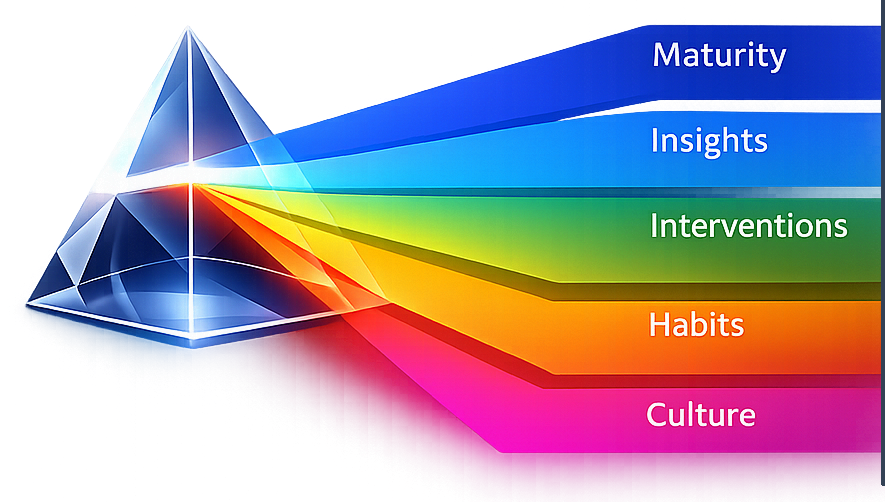
PRISM
A strategic intelligence platform that measures your security culture through two complementary frameworks: Maturity Analysis (how capable is your programme?) and Culture Formation (how embedded are the practices?). PRISM uses scientifically validated surveys to gather insights from employees, then analyses responses through multiple analytical engines to deliver actionable intelligence that measurably improves your security culture.
